一、SSH 概述
1.SSH 简介
SSH(secure Shell)是一种安全通道协议,主要用来实现字符界面的远程登录、远程复制等功能。SSH 协议对通信双方的数据传输进行了加密处理,其中包括用户登录时输入的用户口令,与 Telnt(远程登陆)等应用相比,SSH 协议提供了更好的安全性。
2.默认监听端口:
TCP 22
二、OpenSSH 的配置
1.OpenSSH 安装包
默认安装 Linux 系统时自动安装,若未安装,安装光盘中的如下 rpm 包
openssh-7.4p1-16.el7.x86_64.rpm
openssh-clients-7.4p1-16.el7.x86_64.rpm
openssh-server-7.4p1-16.el7.x86_64.rpm
openssh-askpass-7.4p1-16.el7.x86_64.rpm
- 服务名称:sshd
- 服务的主程序:/usr/sbin/sshd
- 服务端配置文件:/etc/ssh/sshd_config
- 客户端配置文件:/etc/ssh/ssh_config
2.服务端 OpenSSH 配置
[root@huyouba1 ~]# cd /etc/ssh/
[root@huyouba1 ssh]# ls
moduli sshd_config ssh_host_ecdsa_key.pub ssh_host_ed25519_key.pub ssh_host_rsa_key.pub
ssh_config ssh_host_ecdsa_key ssh_host_ed25519_key ssh_host_rsa_key
[root@huyouba1 ssh]# cp -p sshd_config sshd_config.$(date +%F-%T)
[root@huyouba1 ssh]# vim sshd_config
17 #Port 22 //默认端口,tcp22
18 #AddressFamily any //指定地址簇,any,inet(ipv4),inet6(ipv6)
19 ListenAddress 192.168.100.100 //监听IP,默认0.0.0.0,监听所有
37 LoginGraceTime 2m //等待登录时长2分钟
38 PermitRootLogin yes //默认允许root用户登录
39 StrictModes yes //接受连接请求前,对用户的目录和相关配置文件进行宿主化和权限检查
40 MaxAuthTries 6 //最大允许认证次数
41 MaxSessions 10 //每个网络允许打开会话的最大数量
42 RSAAuthentication yes //启用RSA验证
43 PubkeyAuthentication yes //启用密钥对验证
47 AuthorizedKeysFile .ssh/authorized_keys//指定公钥库位置
64 PermitEmptyPasswords no //不允许空密码用户登录
65 PasswordAuthentication yes //启用密码验证
115 UseDNS no //禁用反向解析
手动添加:
140 AllowUsers huyouba1 zhangsan@192.168.100.2 root
141 #DenyUsers lisi
AllowUsers:用户 huyouba1、root在任何客户端均可登录;用户 zhangsan 只允许在IP地址为192.168.100.2的客户端登录。和仅允许此三用户通过ssh协议远程登录。
DenyUsers:禁止用户lisi登录注意:AllowUsers不要与DenyUsers同时使用
修改配置文件后,重启sshd服务
[root@huyouba1 ssh]# systemctl restart sshd
三、使用 SSH 客户端程序
1.命令程序:
(1)ssh 命令(远程安全登录)
格式:ssh user@host(若客户机与主机用户名相同,可省去@)
端口选项:-p 22
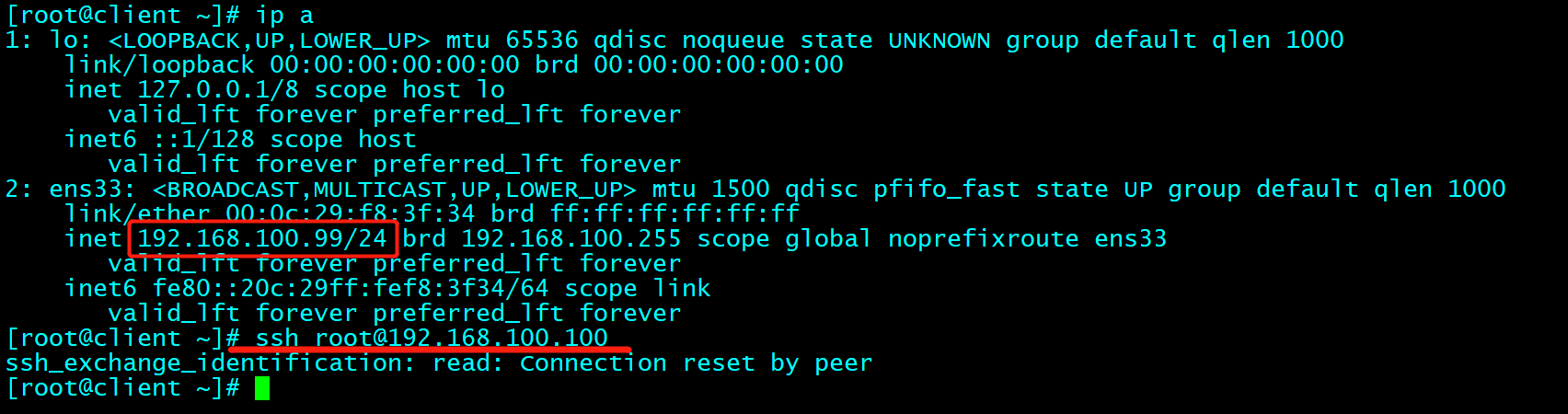
[root@huyouba1 ssh]# hostnamectl set-hostname server-SSH.huyouba1.com
[root@huyouba1 ssh]# bash
[root@server-ssh ssh]# useradd huyouba1
[root@server-ssh ssh]# echo 123123 |passwd --stdin huyouba1 &>/dev/null
[root@client ~]# useradd admin
[root@client ~]# echo 123123|passwd --stdin admin &>/dev/null
[root@client ~]# su - admin
[admin@client ~]$ ssh huyouba1@192.168.100.100
The authenticity of host '192.168.100.100 (192.168.100.100)' can't be established.
ECDSA key fingerprint is SHA256:EyJfW4SjGSVwhejnsPqUDEiWwuNDyHsSdVWGMjXGAQ0.
ECDSA key fingerprint is MD5:76:b8:ff:17:f1:c7:4c:c2:2d:9d:9b:33:51:6c:aa:e6.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.100.100' (ECDSA) to the list of known hosts.
huyouba1@192.168.100.100's password:
Last failed login: Sun Mar 22 12:28:10 CST 2020 from 192.168.100.102 on ssh:notty
There were 2 failed login attempts since the last successful login.
[huyouba1@server-ssh ~]$ whoami
huyouba1
[huyouba1@server-ssh ~]$ 登出
Connection to 192.168.100.100 closed.
(2)scp 命令(远程安全复制)
格式1:scp user@host:file1 file2
格式2:scp file1 user@host:file2
1> 从服务端复制文件到客户端
服务端:
[root@server-ssh ssh]# cd
[root@server-ssh ~]# mkdir /aaa
[root@server-ssh ~]# touch /aaa/test{1..10}
[root@server-ssh ~]# ls /aaa/
test1 test10 test2 test3 test4 test5 test6 test7 test8 test9
[root@server-ssh ~]#
客户端:
[root@client ~]# rm -rf /bbb/
[root@client ~]# mkdir /bbb
[root@client ~]# ls /bbb
[root@client ~]# scp huyouba1@192.168.100.100:/aaa/* /bbb
The authenticity of host '192.168.100.100 (192.168.100.100)' can't be established.
ECDSA key fingerprint is SHA256:EyJfW4SjGSVwhejnsPqUDEiWwuNDyHsSdVWGMjXGAQ0.
ECDSA key fingerprint is MD5:76:b8:ff:17:f1:c7:4c:c2:2d:9d:9b:33:51:6c:aa:e6.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.100.100' (ECDSA) to the list of known hosts.
huyouba1@192.168.100.100's password:
test1 100% 0 0.0KB/s 00:00
test10 100% 0 0.0KB/s 00:00
test2 100% 0 0.0KB/s 00:00
test3 100% 0 0.0KB/s 00:00
test4 100% 0 0.0KB/s 00:00
test5 100% 0 0.0KB/s 00:00
test6 100% 0 0.0KB/s 00:00
test7 100% 0 0.0KB/s 00:00
test8 100% 0 0.0KB/s 00:00
test9 100% 0 0.0KB/s 00:00
[root@client ~]# ls /bbb
test1 test10 test2 test3 test4 test5 test6 test7 test8 test9
[root@client ~]#
2> 从客户端复制文件到服务端
客户端:
[root@client ~]# echo ceshi >client.txt
[root@client ~]# scp client.txt huyouba1@192.168.100.100:~huyouba1/client1.txt
huyouba1@192.168.100.100's password:
client.txt 100% 6 7.0KB/s 00:00
[root@client ~]#
服务端:
[root@server-ssh ~]# ll ~huyouba1/
总用量 4
-rw-r--r-- 1 huyouba1 huyouba1 6 3月 22 12:41 client1.txt
(3)sftp 命令(安全 FTP 上传下载)
格式:sftp user@host
客户端:
[root@client ~]# mkdir /ccc
[root@client ~]# cd /ccc/
[root@client ccc]# ls
[root@client ccc]# sftp huyouba1@192.168.100.100
huyouba1@192.168.100.100's password:
Connected to 192.168.100.100.
sftp> ls /aaa/
/aaa/test1 /aaa/test10 /aaa/test2 /aaa/test3 /aaa/test4 /aaa/test5 /aaa/test6 /aaa/test7 /aaa/test8 /aaa/test9
sftp> mget /aaa/*
Fetching /aaa/test1 to test1
Fetching /aaa/test10 to test10
Fetching /aaa/test2 to test2
Fetching /aaa/test3 to test3
Fetching /aaa/test4 to test4
Fetching /aaa/test5 to test5
Fetching /aaa/test6 to test6
Fetching /aaa/test7 to test7
Fetching /aaa/test8 to test8
Fetching /aaa/test9 to test9
sftp> exit
[root@client ccc]# ls
test1 test10 test2 test3 test4 test5 test6 test7 test8 test9
[root@client ccc]#
常见远程访问工具:Xshell、CRT、Putty、Xmanager(远程图形化界面)等
四、构建密钥对验证的 SSH 体系
1.在客户端创建密钥对 ssh-keygen 命令
可用的加密算法:RSA 或 DSA
[root@client ccc]# su - admin
上一次登录:日 3月 22 12:40:24 CST 2020pts/0 上
[admin@client ~]$ ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/admin/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/admin/.ssh/id_rsa.
Your public key has been saved in /home/admin/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:AqZel6dqawMt0Pzq1saBJAmMcrf9wxABTqQGCenU4Ng admin@client
The key's randomart image is:
+---[RSA 2048]----+
|*+o.+... |
|O=.=. . |
|**E.+o . |
|+o+o..o. |
| +.+. ++S |
| .+.+. ++ |
| .* .. . |
| o B. |
| o.+oo |
+----[SHA256]-----+
[admin@client ~]$ ls .ssh/
id_rsa id_rsa.pub known_hosts
[admin@client ~]$
2.将公钥上传至服务器
(1)方法一:任何方式均可(共享,FTP,电子邮件,SCP,……)
客户端:
[admin@client ~]$ scp .ssh/id_rsa.pub huyouba1@192.168.100.100:~huyouba1/
huyouba1@192.168.100.100's password:
id_rsa.pub 100% 394 408.8KB/s 00:00
[admin@client ~]$
服务端:在服务器中导入公钥文本
[root@server-ssh ~]# su - huyouba1
上一次登录:日 3月 22 12:40:38 CST 2020从 192.168.100.102pts/1 上
[huyouba1@server-ssh ~]$ ls
client1.txt id_rsa.pub
[huyouba1@server-ssh ~]$ mkdir .ssh
[huyouba1@server-ssh ~]$ chmod 700 .ssh/
[huyouba1@server-ssh ~]$ cat id_rsa.pub >>.ssh/authorized_keys
[huyouba1@server-ssh ~]$ cat .ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDCrcRJsJGZBwrtoVZ+t+SStNkJJg8mgyyrGqtCOefwWwfd115OnUPJbWxGpYG1toYtq1Bs5gpsfsiHGJvxZnQlFt5ileHwMXdtSrv6H5/jA/CpLlGpNlJJsAoobmC5rvctKwwU+obGfCCnKkJOwkyG2ef37lumN+6F7Ls1UgHRY9l0tdF9k7B9nxXMFGcAo3sZ/cCEpAHRbSoJL43wYlRxkpWIPnw+e8MEswWGGcR8ZlR3d/EaZ2+XQ6ZRqlJ/Zd2bgmiT2l7boPG0RJySVokQL0Nt9rb2nYUdaOhnxyn/lsIm3xbLVi7MgSETIJredP2RHpGrp1vBBi29oEitxQqR admin@client
[huyouba1@server-ssh ~]$
(2)方法二:ssh-copy-id 命令
服务端删除签名拷贝的公钥文件
[huyouba1@server-ssh ~]$ rm -rf .ssh/authorized_keys
客户端:
[admin@client ~]$ ssh-copy-id -i .ssh/id_rsa.pub huyouba1@192.168.100.100
/bin/ssh-copy-id: INFO: Source of key(s) to be installed: ".ssh/id_rsa.pub"
/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
huyouba1@192.168.100.100's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'huyouba1@192.168.100.100'"
and check to make sure that only the key(s) you wanted were added.
[admin@client ~]$
服务端:
[huyouba1@server-ssh ~]$ ll .ssh/
总用量 4
-rw------- 1 huyouba1 huyouba1 394 3月 22 12:59 authorized_keys
[huyouba1@server-ssh ~]$ cat .ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDCrcRJsJGZBwrtoVZ+t+SStNkJJg8mgyyrGqtCOefwWwfd115OnUPJbWxGpYG1toYtq1Bs5gpsfsiHGJvxZnQlFt5ileHwMXdtSrv6H5/jA/CpLlGpNlJJsAoobmC5rvctKwwU+obGfCCnKkJOwkyG2ef37lumN+6F7Ls1UgHRY9l0tdF9k7B9nxXMFGcAo3sZ/cCEpAHRbSoJL43wYlRxkpWIPnw+e8MEswWGGcR8ZlR3d/EaZ2+XQ6ZRqlJ/Zd2bgmiT2l7boPG0RJySVokQL0Nt9rb2nYUdaOhnxyn/lsIm3xbLVi7MgSETIJredP2RHpGrp1vBBi29oEitxQqR admin@client
[huyouba1@server-ssh ~]$
3.在客户端使用密钥对验证
(1)确认服务端配置文件 /etc/ssh/sshd_config 已开启密钥对认证
43 PubkeyAuthentication yes
47 AuthorizedKeysFile .ssh/authorized_keys
(2)客户端使用密钥对验证登录:
[admin@client ~]$ ssh huyouba1@192.168.100.100
The authenticity of host '192.168.100.100 (192.168.100.100)' can't be established.
ECDSA key fingerprint is SHA256:EyJfW4SjGSVwhejnsPqUDEiWwuNDyHsSdVWGMjXGAQ0.
ECDSA key fingerprint is MD5:76:b8:ff:17:f1:c7:4c:c2:2d:9d:9b:33:51:6c:aa:e6.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.100.100' (ECDSA) to the list of known hosts.
Last login: Thu Mar 26 12:21:52 2020 from 192.168.100.102
[huyouba1@server-ssh ~]$
五、TCP Wrappers
1.TCP Wrappers 保护原理
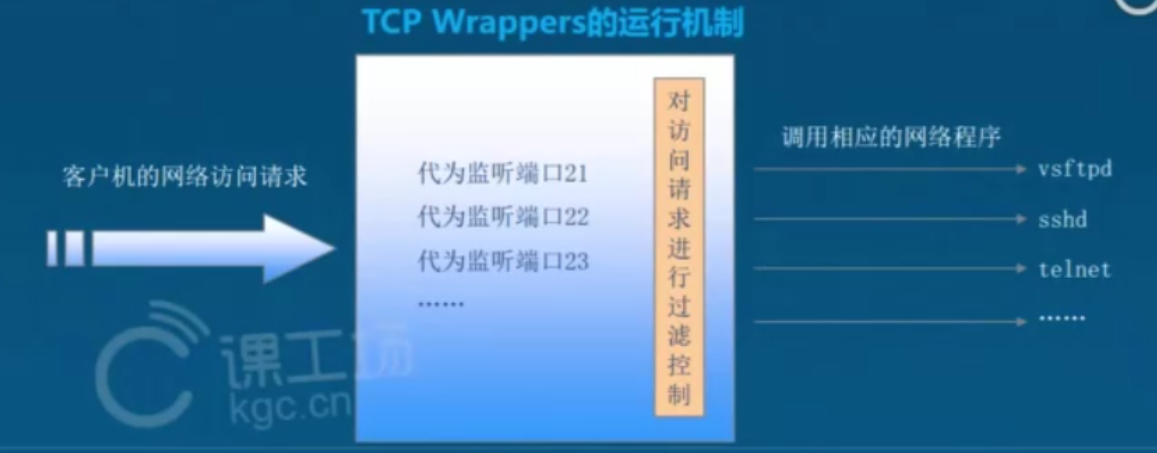
2.保护机制的实现方式
方式1:通过 tcpd 主程序对其他服务程序进行包装
方式2:由其他服务程序调用 libwrap.so.*链接库
3.TCP Warppers 保护的条件
- 必须是采用 TCP 协议的服务
- 函数库中必须包含 libwrap.so.0(可用 ldd 命令查看)
[root@server-ssh ~]# which sshd
/usr/sbin/sshd
[root@server-ssh ~]# ldd /usr/sbin/sshd |grep libwrap
libwrap.so.0 => /lib64/libwrap.so.0 (0x00007fbdd971b000)
[root@server-ssh ~]# which httpd
/usr/sbin/httpd
[root@server-ssh ~]# which httpd |grep libwrap
[root@server-ssh ~]#
由此可见,sshd 服务可以采用 TCP wrappers 进行保护,而 httpd 服务虽然也是采用 TCP 协议,但无法使用 TCP Wrappers 进行保护。
4.访问控制策略的配置文件
/etc/hosts.allow
/etc/hosts.deny
[root@server-ssh ~]# ll /etc/hosts.*
-rw-r--r--. 1 root root 370 6月 7 2013 /etc/hosts.allow
-rw-r--r--. 1 root root 460 6月 7 2013 /etc/hosts.deny
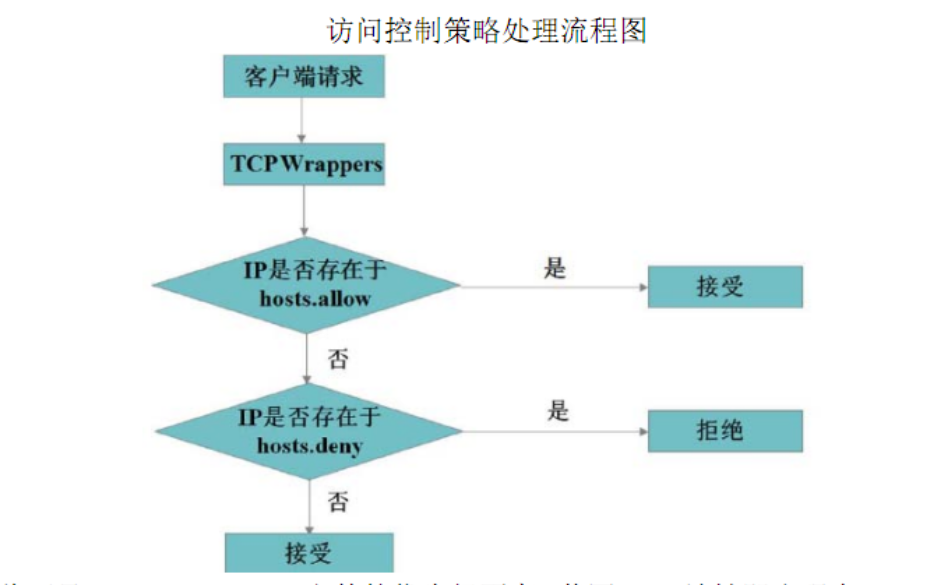
由此可见,/etc/hosts.allow 文件的优先级更高,若同一 IP 地址即出现在 hosts.allow 中,也存在于 hosts.deny 中,则该 IP 地址的访问请求将被接受。
5.配置项及格式
(1)格式:
服务列表:客户机地址列表
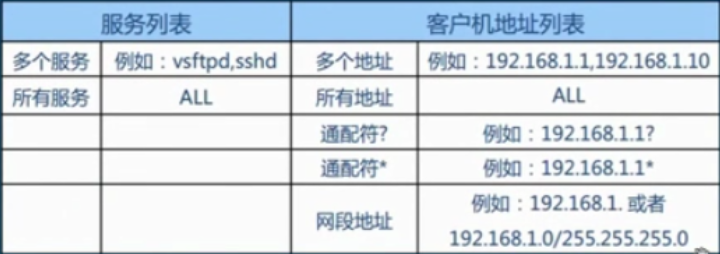
(2)通配符
1> 通配符 ?:每一个?表示1位任意数字。如192.168.1.1?表示192.168.1.10~192.168.1.19; 192.168.1.1 ??表示192.168.100~192.168.1.199
2> 通配符 *:表示任意位数,也可为空。如192.168.1.1表示192.168.1.1,192.168.1.10~192.168.1.19,192.168.1.100~192.168.1.199 (3)配置示例 实验要求:仅允许 IP 地址为 192.168.100.100 ~ 192.168.100.199 的主机访问 sshd 服务,禁止其他所有地址的访问。
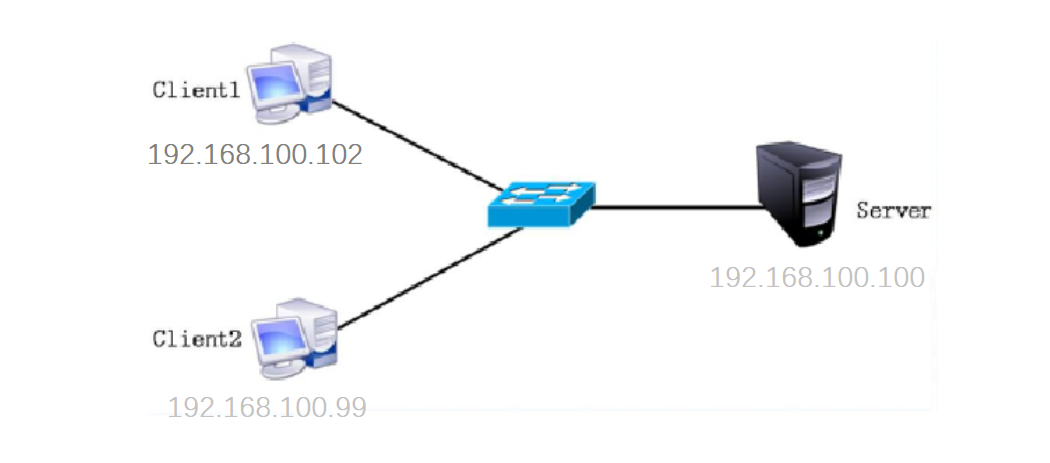
[root@server-ssh ~]# echo "sshd:192.168.100.1??" >>/etc/hosts.allow
[root@server-ssh ~]# echo "sshd:ALL" >>/etc/hosts.deny
[root@server-ssh ~]# tail -1 /etc/hosts.allow
sshd:192.168.100.1??
[root@server-ssh ~]# tail -1 /etc/hosts.deny
sshd:ALL
客户机 client1 测试
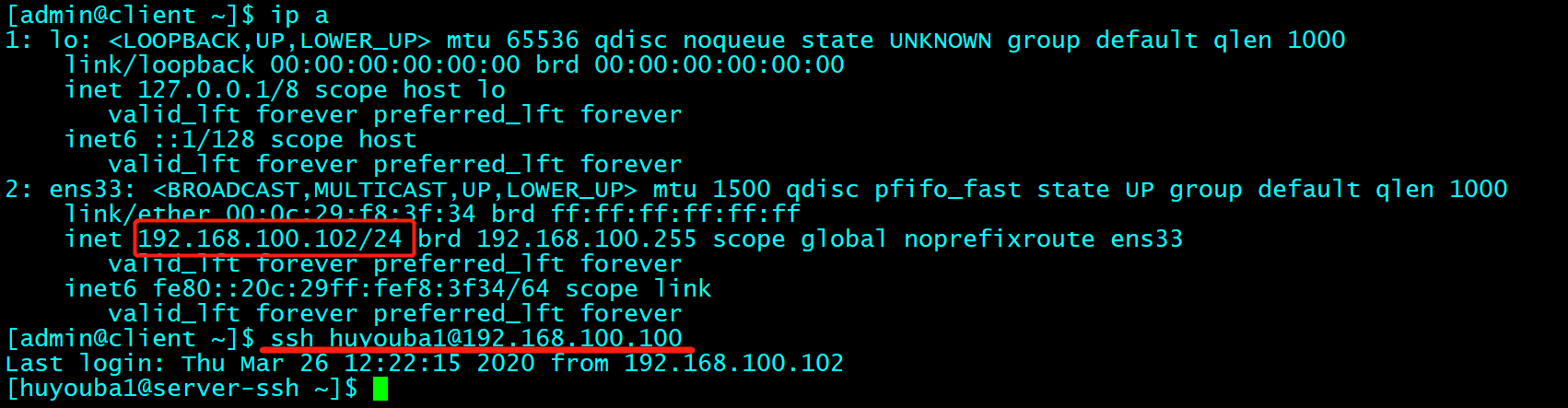
客户机 client2 测试